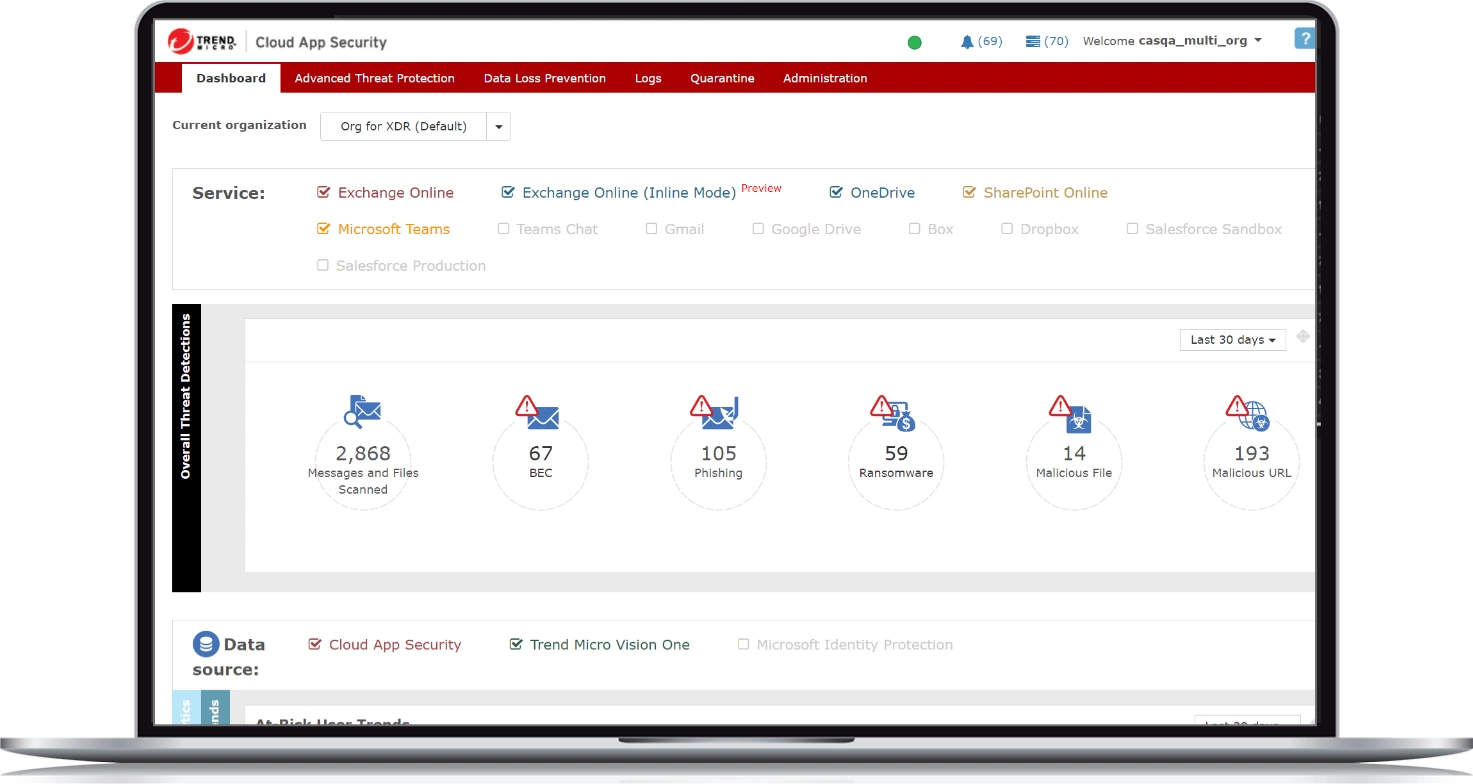
Office 365 security
Uncovers ransomware, business email compromise (BEC), and other malicious attacks. Finds malware through pre-execution machine learning and artificial intelligence. Checks email behavior, intention, and authorship to identify BEC attacks. Blocks threats beyond those detected by cloud email services’ built-in security.

Superior detection and response
Trend Micro™ Deep Discovery™ detects malware and shares intelligence with other security layers. Pre-filter technology prevents delays. Additional extended detection and response (XDR) capabilities identify and stop malware. Trend Micro™ Cloud App Security detects attacks already in progress and criminal infiltration attempts.

Simple integration and management
Simple API integration. Manage threat and Data Loss Prevention (DLP) activity across cloud services, endpoints, and web traffic. Sandbox analysis exports indicators of compromise (IoC) to Trend Micro to prevent attacks. Cloud App Security APIs bolster detection and response to threats.
WHY CLOUD APP SECURITY
Detect, identify, and respond to threats across your company's cloud ecosystem.
Leverage multiple defense techniques
Enhance the security of Office 365, Google Workspace, and other cloud services by leveraging sandbox malware analysis for ransomware, BEC, and advanced threats. The security included with Office 365 filters known antivirus threats, but 95% of today’s malware will only infect one device and is unknown to traditional antivirus techniques.
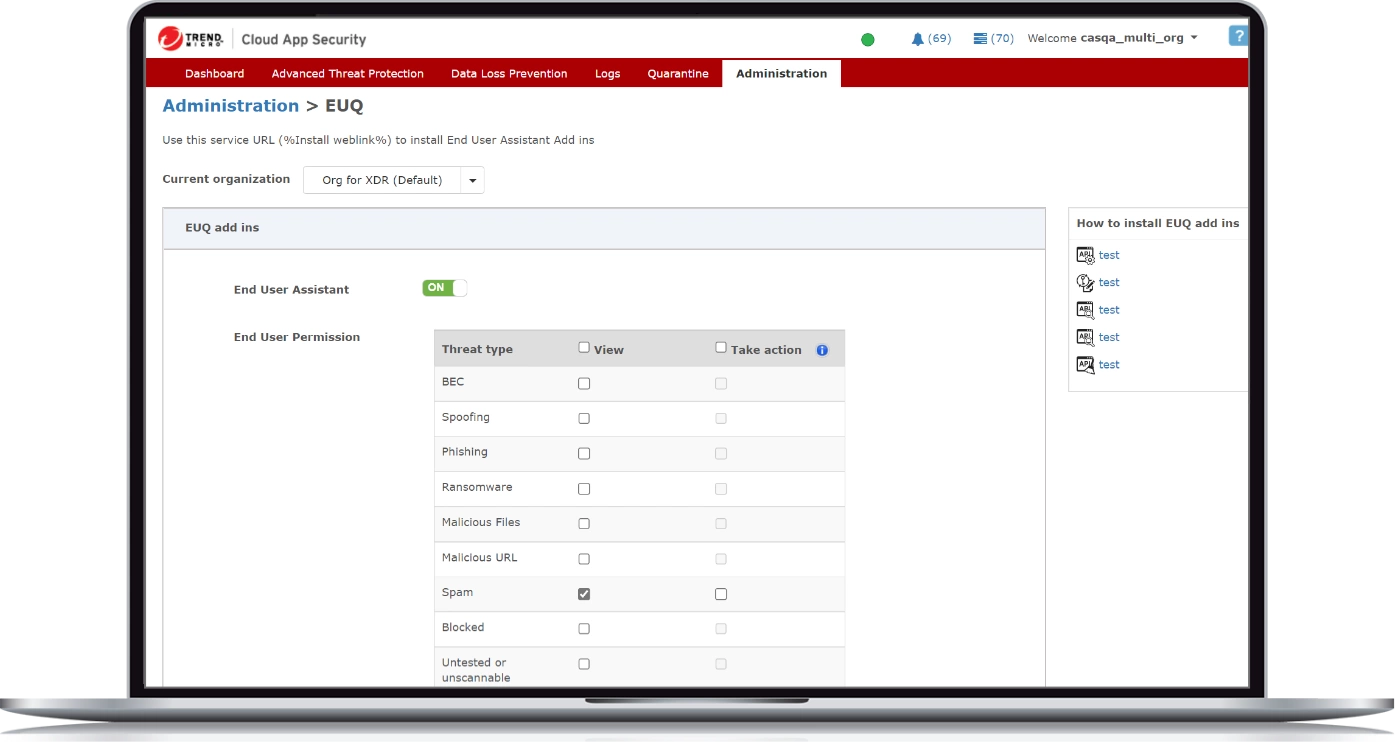
Monitor and protect sensitive data
Control sensitive data usage: DLP for Microsoft® OneDrive® for Business, Microsoft® SharePoint® Online, Microsoft® Teams, Dropbox™, Box™, and Google Drive™. Cloud App Security uses 200+ pre-built, customizable compliance templates to control data sharing. It protects your shared files from malware and scans files shared remotely to prevent infiltration through cloud file-sharing and collaborative services.
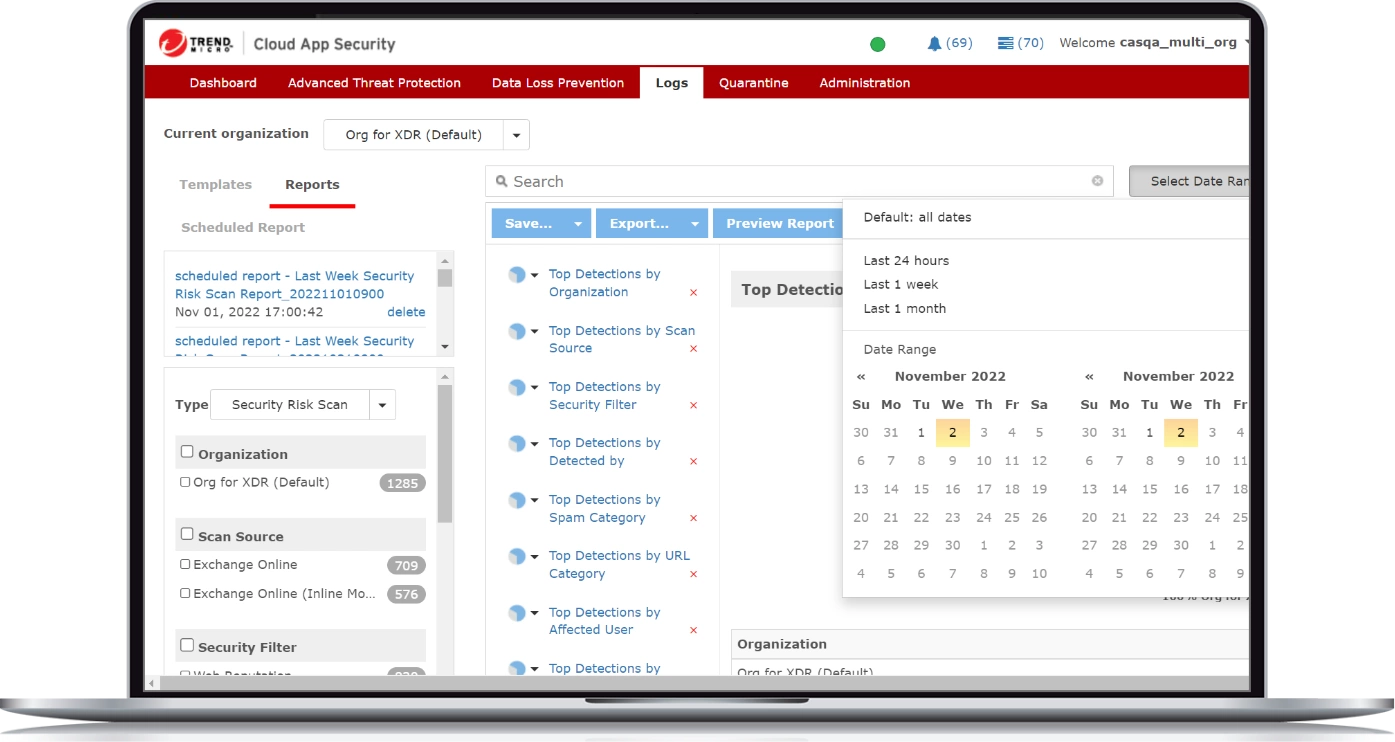
Extended detection and response
Identifying compromised accounts and detecting malicious emails is critical to threat detection. Trend Vision One™ helps security analysts:
- Trace a root cause analysis of a threat, identify the impact, and stop the spread
- Sweep inboxes for IoC and quarantine or delete emails
- Correlate detection, investigation, and response
- Access advanced email XDR capabilities
- Employ our MDR service

See what our customers have to say on Gartner Peer Insights
Trusted security partner

Explore related resources
JOIN 500K+ GLOBAL CUSTOMERS
Get started with Cloud App Security